Use Internal URLs to access apps from anywhere with our My Apps Sign-in Extension and the Azure AD Application Proxy
Hi Folks,
I’m excited to share the news that your users can now access applications through internal URLs even when outside your corporate network by using the My Apps Secure Sign-in Extension for Azure AD . When a user types in a familiar shorthand URL such as https://traveldashboard, they can be redirected to the externally resolvable URL, https://www.traveldashboard.adventure-works.com. This will work with any application that you have published using Azure AD Application Proxy, on any browser that also has the Access Panel browser extension installed.
To try it out, get the latest version of the extension (currently supported on Chrome, and Firefox). Then, type the internal URL of the published application into the address bar. The extension will recognize that the URL has been published through Application Proxy and will redirect you to the external URL of the application.
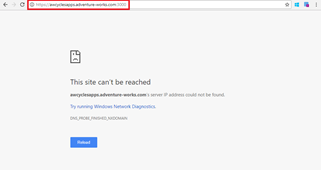
Without the extension, when someone is outside your corporate network, the only way to reach this application remotely was to use a specific external URL. Trying the “normal” internal URL resulted in an error.

Accessing using the internal URL

Accessing using the external URL
With the extension, you can now to go the internal URL and will be directed to the working external URL.


Users can download our extension themselves, or admins can deploys the extension using the browser’s group policy settings. The URL redirection functionality is automatically enabled once a user logs into the extension.
Visit our documentation to learn more about this feature, and how it compares to some of our previous URL mapping recommendations such as custom domains. We have already recently added documentation for some applications we frequently get questions about, such as Tableau and Qlik Sense.
As always, we’d love to receive any feedback or suggestions you have! Head over to our feedback forum or email us at aadapfeedback@microsoft.com.
Best Regards,
Alex Simons (Twitter: @Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
Source: EM+S Blog Feed