Prioritize user investigations in Cloud App Security
This week we announced a new Identity threat investigation experience, which correlates identity events from Microsoft Cloud App Security, Azure Advanced Threat Protection, and Azure Active Directory Identity Protection into a single investigation experience for security analysts and hunters alike.
If you are using Microsoft Cloud App Security, you will be able to access the new experience in the portal starting today, regardless of whether you are also using Azure Advanced Threat Protection and/or Azure Active Directory Identity Protection.*
The identity threat investigation experience combines user identity signals from on-premises and cloud services to close the gap between disparate signals in your environment and leverages state-of-the-art User and Entity Behavior Analytics (UEBA) capabilities to provide a risk score and rich contextual information for each user. It empowers security analysts to prioritize their investigations and reduce investigation times, ending the need to toggle between identity security solutions.
New user investigation priority for users
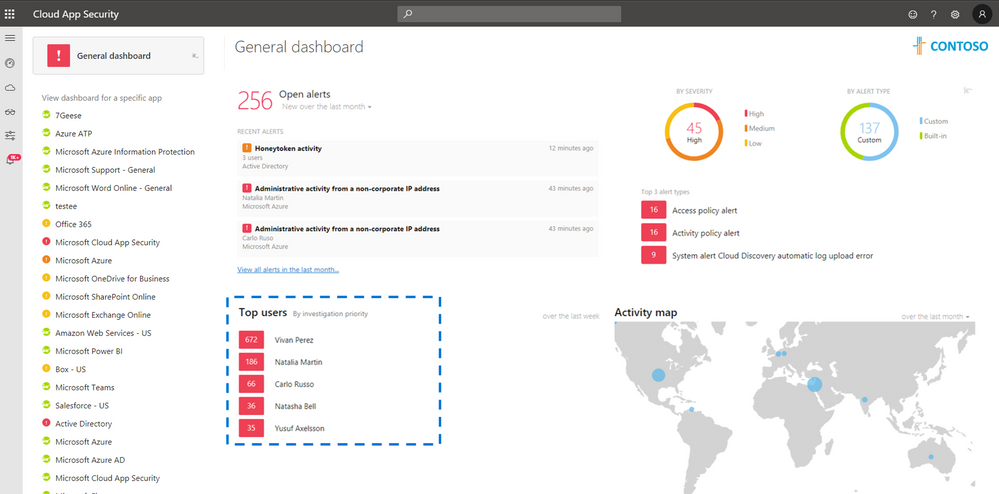
The Top user view in the Microsoft Cloud App Security dashboard is shifting from an investigation model that is based on the number of total alerts, to a new user investigation priority which is determined by all recent user activities and alerts that indicate an active attack or insider threat. This now helps you immediately understand which users currently represent the highest risk within your organization and should be prioritized for further investigation.
New user page
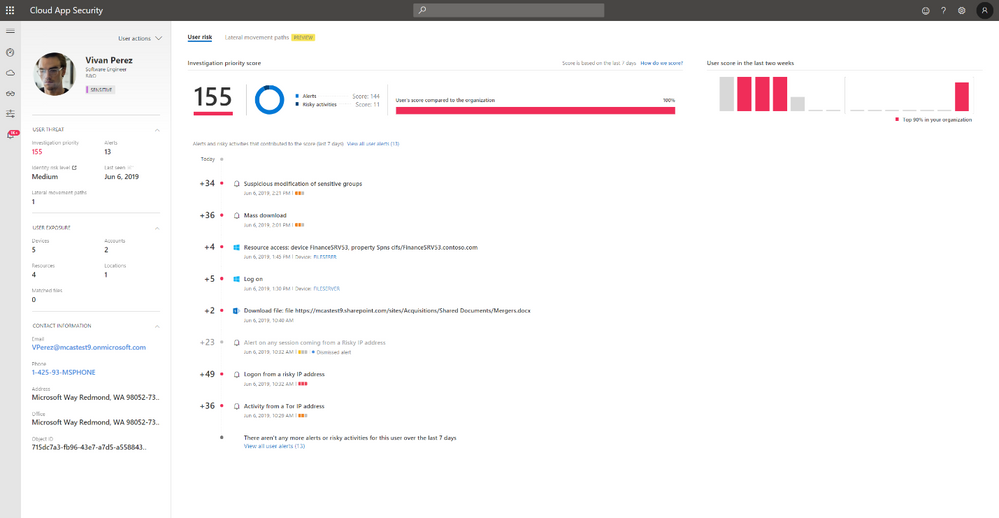
We have also redesigned the existing user page to provide rich contextual information for how the risk score was determined and how a user compares to other across the organization. This will empower your SOC teams to address the users with the highest risk/impact ratio first and pivot from any scored activity into the deep dive alert investigation that you’re already familiar with.
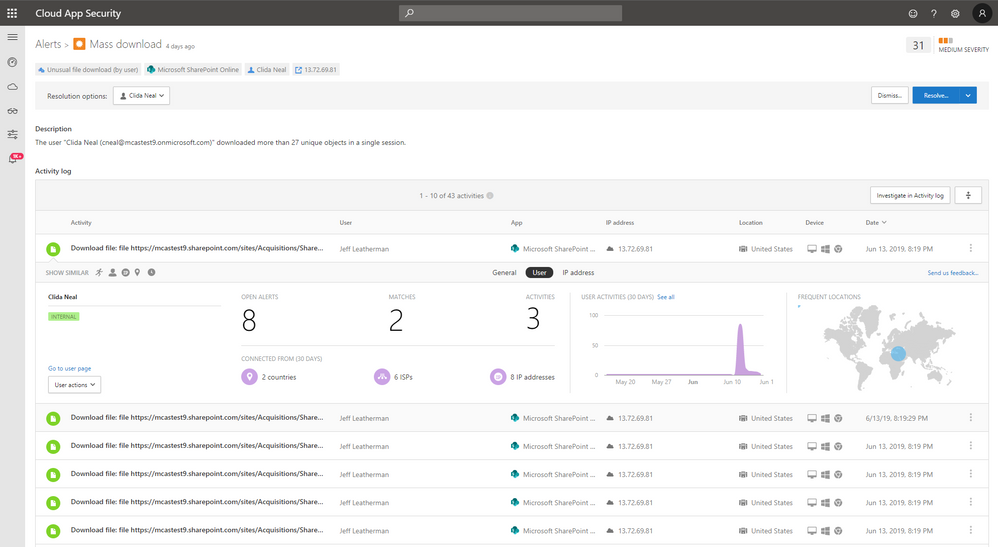
From the new user page, you can then easily dive deeper into each one of the alerts or activities that you see on the timelines and pivot into the Cloud App Security investigation experience that you’re already familiar with.
The new Identity threat investigation experience further enriches the Cloud App Security portal and available investigation capabilities, giving SecOps teams correlated and weighted information to make better decisions, save time and more effectively remediate user threats and risks.
More info and feedback
Get started with our technical documentation today.
- Haven’t tried Microsoft Cloud App Security yet? Start a free trial today.
- As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.
- For more resources and information go to our website.
*The information available on the new user page can vary depending on the services that you are using (Azure Advanced Threat Protection, Azure AD Identity Protection)
Source: EM+S Blog Feed