General availability of VNet Service Endpoints for Azure SQL Data Warehouse
This blog post was co-authored by Anitha Adusumilli, Principal Program Manager, Azure Networking.
We’re excited to share the general availability of Virtual Network (VNet) Service Endpoints for Azure SQL Data Warehouse in all Azure regions. Azure SQL Data Warehouse is a fast, flexible, and secure cloud data warehouse tuned for running complex queries fast and across petabytes of data.
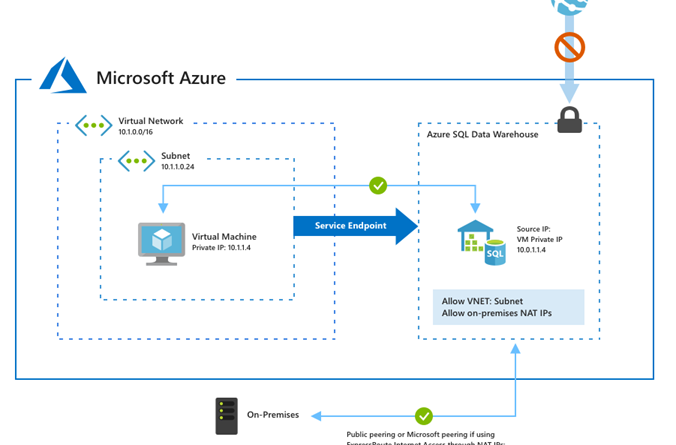
VNet Service Endpoints enable you to isolate connectivity to your logical server from a given subnet or set of subnets within your virtual network. The traffic to Azure SQL Data Warehouse from your VNet will always stay within the Azure backbone network. This direct route will be preferred over any specific routes that take Internet traffic through virtual appliances or on-premises. There is no additional billing for virtual network access through service endpoints. Current pricing model for Azure SQL Data Warehouse applies as is.
With this release, we also enabled PolyBase connectivity to Azure Data Lake Storage Gen2 (ADLS) via Azure Blob File System (ABFS) driver. Azure Data Lake Storage Gen2 brings all the qualities that are required for the full lifecycle of analytics data to Azure Storage. It is the result of converging the capabilities of our two existing storage services, Azure Blob Storage, and Azure Data Lake Storage Gen1. Features from Azure Data Lake Storage Gen1, such as file system semantics, file-level security, and scale are combined with low-cost, tiered storage, and high availability/disaster recovery capabilities from Azure Blob Storage.
Using Firewall rules and VNet Service Endpoints together
Turning on VNet Service Endpoints does not override Firewall rules that you have provisioned on your logical SQL Server or Azure SQL Data Warehouse. Both continue to be applicable.
VNet Service Endpoints don’t extend to on-premises. To allow access from on-premises, Firewall rules can be used to limit connectivity only to your public (NAT) IPs.
To enable VNet protection, first enable service endpoints for SQL in the VNet as follows:
On the logical SQL Server, you can allow access to multiple subnets belonging to one or more VNets. It is also possible for you to configure Firewall rules in conjunction to your VNet rules.
PolyBase connectivity to Azure storage account secured to VNet
With this release, we also enabled Polybase connectivity to Azure storage account secured to VNet. Please follow steps described in this guide for enabling PolyBase import and export scenarios with Azure storage account secured to VNet.
Turning on service endpoints for servers with pre-existing firewall rules
When you connect to your server with service endpoints turned on, the source IP of SQL connections will switch to the private IP space of your VNet. If at present, your server or database firewall rules allow specific Azure public IPs, then the connectivity will break until you allow the given VNet/subnet by specifying it in the VNet firewall rules. To ensure connectivity, you can preemptively specify VNet firewall rules before turning on service endpoints by using IgnoreMissingVNetServiceEndpoint flag.
Next steps
- To get started, refer to our documentation, “Virtual Network Service Endpoints” and “VNet Service Endpoints and rules for Azure SQL Data Warehouse.”
- For more information about Azure SQL Data Warehouse security capabilities, refer to the “Guide to enhancing privacy and addressing GDPR requirements with the Microsoft SQL platform” from the Microsoft Trust Center, or our online documentation.
- To provision, refer to create an Azure SQL Data Warehouse document.
- To stay up-to-date on the latest Azure SQL Data Warehouse news and features, follow us on Twitter @AzureSQLDW.
- For feature requests, please vote on our UserVoice.
- For more information on the Azure Data Lake Storage Gen2 updates, refer to this blog.
Source: Azure Blog Feed