LDAP Reconnaissance – the foundation of Active Directory attacks
When an attacker manages to break into an on-premises domain environment, one of the first steps they normally take is to gather information and perform domain reconnaissance. Reconnaissance involves identifying the users, resources and computers in the domain and then building an understanding of how those resources are used to form your domain environment.
While an attacker can gather data without credentials, research has revealed that most of the time, attackers make use of normal, non-privileged, domain user rights to make their moves.
How do LDAP-based attacks succeed if security is in place?
In most environments, every account in the domain has the permissions needed to perform reconnaissance using the LDAP protocol, and LDAP is deployed as a default part of domain controller services. With the default configuration in place, any domain user can retrieve domain configurations, such as where exchange servers are installed, or get account related details, such as Domain Admin group membership lists, as well as details about which account can delegate authentication, what users have a Kerberos principal name, and more.
Aside from user accounts, most on-premises domain services use LDAP as a key element for their basic functionality, and group policies are sent to every domain computer over LDAP.
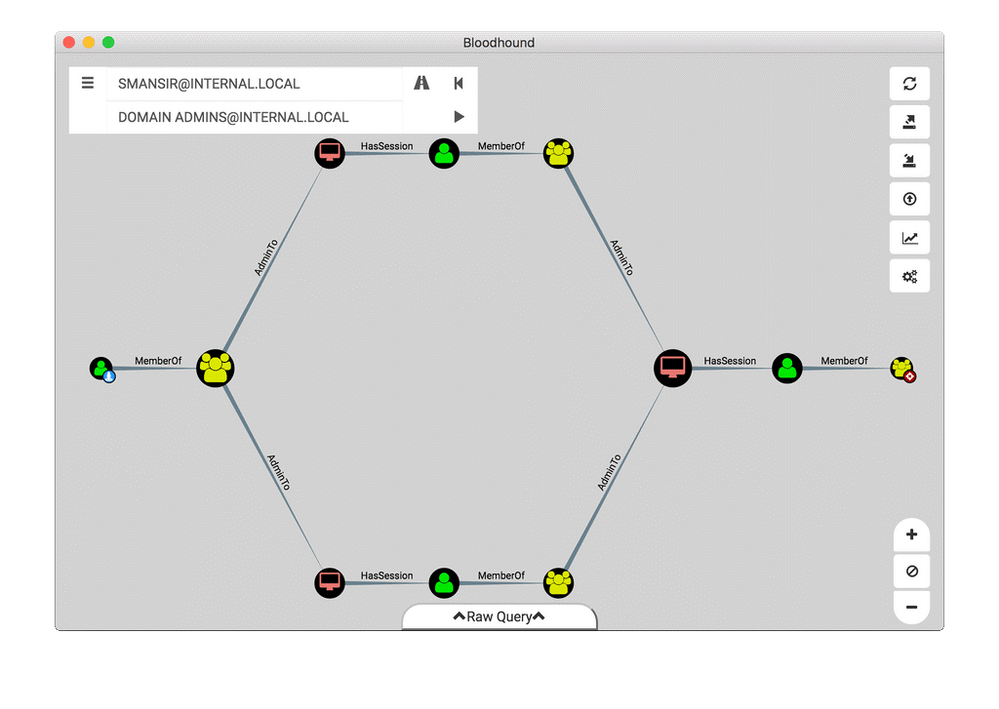
Attackers are known to use LDAP queries to visually map the domain environment using publicly available tools, such as PowerView and BloodHound to implement queries. These tools help get all users, groups, computer accounts and account access control lists (ACL) in the environment. Once the data collected is parsed, it is stored in a graph database and used to build a visual graph that displays the edges between the different accounts, helping the attackers determine and plan their moves laterally in the domain.
Adding standard user account risk to LDAP group policy exposure, you can quickly start to see where LDAP is a potential attack gold mine. By exploiting your LDAP exposure and risk points, attackers find sensitive groups memberships, vulnerable services and map domain account relationships by exploiting any user permissions they can breach or find in your domain.
A single point of failure on a standard user account can be the start of a large-scale breach.
There are also other types of attacks that can be initiated with an LDAP query. Attackers can initiate an internal phishing campaign by enumerating users in Finance or IT groups, harvest private phone numbers that allow them to send phishing links by text message, and find local administrators on end-points computers by retrieving and parsing group polices.
With so many methods and possible attack surfaces, can your domain be protected from LDAP risks?
YES!
To protect your domain, your organization must be able to:
- Define and differentiate between legitimate and malicious activity
- Identify and investigate activity sources and intentions
- Correlate related activities from the same sources
- Discover and remediate compromised accounts
Unprotected LDAP risks leave your entire organization at risk.
Backed by deep data learning modules, Azure Advanced Threat Protection now provides comprehensive LDAP alerts that learn and surface abnormal activities, identify and aid investigation of attack sources, provides correlation of events and suggest remediation steps for compromised accounts.
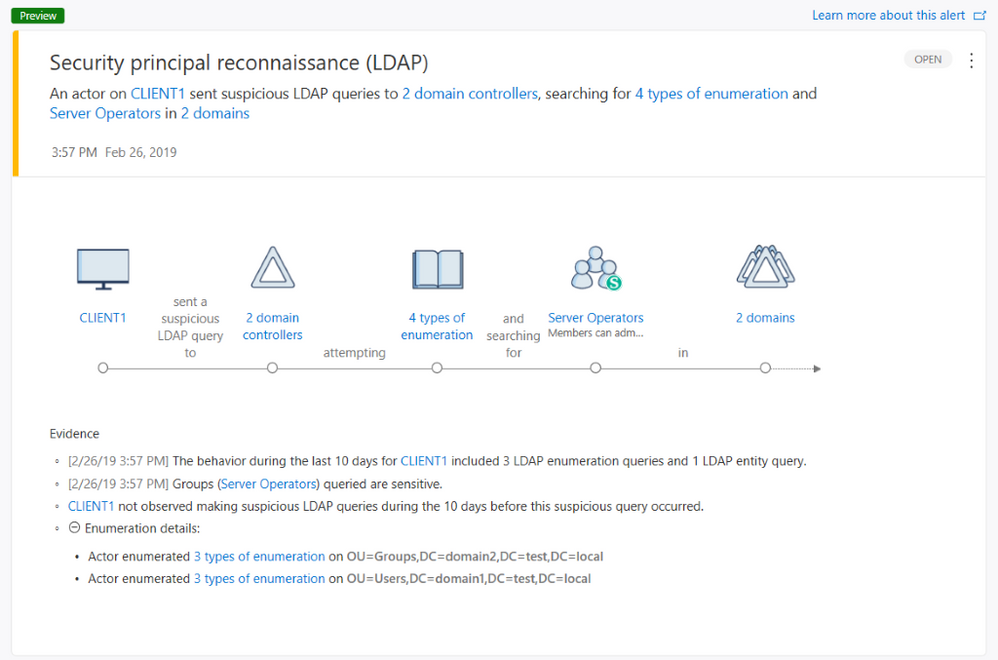
As our security research team continues to develop and refine our threat protection modules and alerts, we welcome your feedback about our work and the security threats and attacks you encounter. We’re excited to hear from you and learn how we can help.
Get Started Today
If you are just starting your journey, begin trials of the Microsoft Threat Protection services today to experience the benefits of the most comprehensive, integrated, and secure threat protection solution for the modern workplace:
- Windows Defender ATP trial
- Office 365 E5 trial
- Enterprise Mobility Suite (EMS) E5 trial
- Azure Security Center trial
Source: EM+S Blog Feed