Integrate Azure Stack into your datacenter
Now that you’ve ordered Azure Stack, how do you integrate it into your datacenter? What are the integration touchpoints?
Introduction
Microsoft Azure Stack is an integrated system available from multiple OEMs. If you haven’t read our blog post about why we decided to go down this path, I encourage you to do so.
Azure Stack offers a tailored, hardened, and secured appliance-like experience with simplified administration. For emergency recovery, a privileged PowerShell endpoint is available, which is secured using just enough administration. The administrative experience has a full-featured update mechanism called Patch and Update (referred as P&U) to ensure that customers can focus on services they run on Azure Stack.
Of course, without being able to integrate into your datacenters, Azure Stack is just an island, consuming power and cooling resources. In this post, I’ll focus on how Azure Stack can integrate into your datacenter.
Network integration
Azure Stack is build using a Clos network topology and uses the Software Defined Network (SDN) capabilities in Windows Server 2016. Azure Stack systems ship with top-of-rack switches and a baseboard management controller switch, which connects the physical server’s baseboard management controller.
All network traffic flowing from the top-of-rack switches to the customer border switches is layer three only. Network traffic is routed using Border Gateway Protocol or static routing, depending on customer requirements.
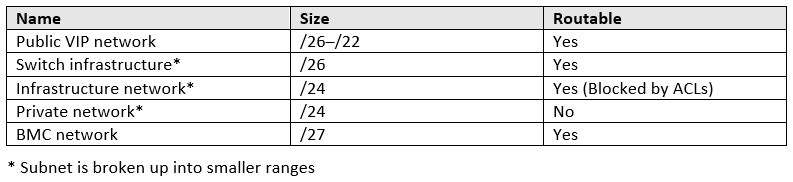
For deployment and integration of Azure Stack, you—as a customer—must offer various IP v4 subnet ranges. While some of them are only used internally by Azure Stack, others are required to be routable within your network and potentially controlled by access control lists (ACLs).
The following table shows a list of required IPv4 Ranges.
Identity
At deployment, you must select either Azure Active Directory (Azure AD) or Active Directory Federation Services (ADFS) to provide identities for Azure Stack. This is a non-revertible decision.
Let’s address the most obvious scenario first: If you run Azure Stack in a completely disconnected scenario (on a boat, for example) then your only choice is ADFS. Also, when deploying with ADFS and Internet connectivity, you can use the consumption-based licensing model of Azure Stack, including marketplace syndication.
Automation in Azure Stack federates an existing ADFS deployment to enable the use of existing on premises identities.
This diagram illustrates the integration:
IT system management
As mentioned earlier, if you don’t integrate Azure Stack with your datacenter, full IT life cycle management is not possible. Azure Stack does not manage your datacenter, but rather it’s a component of your datacenter to be managed. To enable management, it’s key to integrate Azure Stack with your IT system management processes.
Azure Stack systems consists of three major, high-level areas. These three areas are Azure Stack software, physical machines, and physical network switches.
Each area offers a different protocol to retrieve events. For more details see the diagram below:
To accelerate IT system management integration, Microsoft offers a management pack that uses System Center Operations Manager. Microsoft has also co-engineered a plug-in with Nagios to accelerate integration with open-source-based monitoring solutions.
For more information, please read the blog post titled, Management Pack for Microsoft Azure Stack.
Publishing
Azure Stack endpoints can be published in multiple ways, ranging from directly exposed to the Internet, with or without a firewall device—to a traditional DMZ architecture including network address translation.
This illustration shows how Azure Stack can be published directly to the internet with an existing firewall.
Azure Stack handles internal and external DNS zones, which can integrate with existing DNS server environments. Azure Stack includes automation to ensure that name resolution is working for your datacenter resources. However, it does not automatically resolve Azure Stack DNS zones from your existing network, which requires action based on Microsoft recommendations.
SSL certificates, which can be issued by a public trusted root certificate authority or by an enterprise certification authority, must be offered at installation. Furthermore, the deployment accepts either wildcard certificates or multiple certificates with a unique certificate name.
Usage
Azure Stack usage data is tracked under the Azure subscription you provided for registration. You can view your usage data as part of your Azure subscription. In addition, Azure Stack offers an API that allows you to retrieve the same usage data that is sent to Azure. This API is used to integrate with billing systems or panels.
For more information, please see the Provider Resource Usage API page.
Backup
Azure Stack Backup is divided into two scopes: infrastructure backup and tenant backup.
The Azure Stack infrastructure backup requires an SMB file share to operate. This SMB share must be from an existing storage solution (Windows-based file server or third-party). This is considered an “off stamp” backup which enables restoration of infrastructure components or full restoration in case of failure.
For tenant data, Azure Stack supports backup of Windows- and Linux-based applications deployed on IaaS Azure Resource Manager virtual machines. Backup products with access to the guest operating system (OS) can easily protect file, folder, OS state, and application data. You have the flexibility to use Microsoft products like Azure Backup and System Center Data Center Protection Manager to back up data on premises, to a service provider, or directly to Azure. This approach gives you flexibility and choice for protecting your applications and data.
You can read more about backup and disaster recovery for Azure Stack in a future blog post.
Security
If you haven’t had a chance to read the Azure Stack security blog post, I highly recommend you do so. We have designed and built Azure Stack with security in mind, from the ground up, including the ability to exchange audit logs from physical devices and Azure Stack internal components with existing security systems.
The Health Resource Provider API in Azure Stack allows you to retrieve all security logs and make them available to security solutions for processing. For physical devices, RADIUS and TACACS are supported for controlling device authentication and auditing. Azure Stack uses servers deployed in your datacenter to provide these services, including sending syslog messages to existing syslog servers.
Summary
You may have noticed I did not cover solution requirements in terms of power, cooling, rack units, and other typical datacenter requirements. Our OEM partners have those details available, including sizing tools to help you choose the right solution.
More information
Will you be attending Microsoft Ignite this year in Orlando? Check out these two sessions for information about Azure Stack Datacenter Integration:
Lastly, the Azure Stack team is extremely customer focused and we are always looking for new customers to talk too. If you are passionate about Hybrid Cloud and want to talk with team building Azure Stack at Ignite please sign up for our customer meetup.
Source: Azure Stack