How organizations are connecting their on-premises identities to Azure AD
Howdy folks,
If you follow the blog, you know that we support a wide array of options for connecting an on-premises directory or IAM solution to Azure AD. In fact no one in the industry gives customers as many options as we do.
So it’s not surprising that one of the questions customers ask me the most is which one I would recommend. I’m always a bit hesitant to give an answer. Over the last 6+ years working in the identity industry, I’ve learned that every organization is different and has different goals and requirements in terms of speed of deployment, security posture, ability to invest, network architecture, corporate culture, compliance requirements and work environment. That’s one of the reasons why we’ve invested in giving you options, so you can choose the one that best suits your needs. (That doesn’t mean I don’t have an opinion of course – if it was my organization, I’d definitely want to use our new Pass Through Authentication capabilities and Azure AD Connect Sync. They are both fast to deploy and low cost to maintain. But hey, that’s just one person’s opinion!)
Rather than spend a bunch of time worrying about what I or anyone else would recommend, how about we just look at what people are actually using? That always strikes me as the right place to start.
Azure AD Momentum
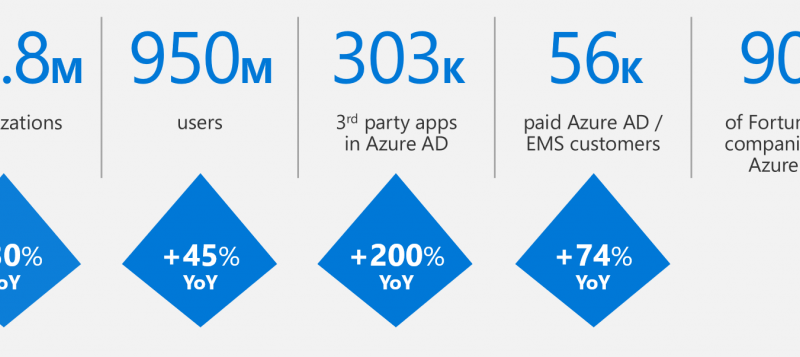
I want to start by sharing some number about the overall use of Azure AD so you have some context for the deeper numbers below. For Azure AD overall, as we continue to see strong growth in organizations using our basic cloud-based identity services and accelerating growth of our Azure AD Premium.
The data I’m the most excited about is the see incredible growth in the use of Azure AD with third-party applications. With over 300k third-party applications in use every month, were seeing organizations turn to Azure AD as the preferred cloud identity platform.
Synching users to Azure AD
Most Azure AD tenants are small organizations that dont synchronize an on-premises AD to Azure AD. Larger organizations almost always sync, and those that do represent >50% of the 950M user accounts in Azure AD.
Heres the latest data on how organizations synchronize users to Azure AD:
- >180K tenants sync their on-premises Windows Server Active Directory to Azure AD .
- >170K tenants use Azure AD Connect to do so.
- A small number of customers use other solutions:
- 7% use our legacy DirSync or Azure AD Sync tools.
- 1.9% use Microsoft Identity Manager or Forefront Identity Manager.
- <1% use a custom or third-party solution.

Authenticating with Azure AD
The last time I blogged about authentications, our data was based on authentication volumes. Your feedback to me was that this made the numbers difficult to put in context and that you were more interested in active user numbers. So, for this update Ill share numbers based on Monthly Active Users (MAU).
As of Oct 31, there were just over 152M Monthly Active Users of Azure AD. Of those active users:
- 55% authenticated using a federation product or service.
- 24% authenticate with Password Hash Sync.
- 21% are cloud only users.
- Azure AD Pass-Through Authentication, which went GA only one month ago, already has over half a million Monthly Active Users and that number is growing at 50% per month!
Diving deeper, heres some more interesting data:
- 46% of all active users are authenticating with AD Federation Services.
- Just over 2% of all active users are authenticating using Ping Federate. Ping is the fastest growing and most popular third-party option.
- 2% of all active users are authenticating using a third-party IDaaS service like Centrify, Okta or OneAuth.
- 1% of all active users are authenticating using a third-party Federation Server other than Ping Federate.

Key Conclusions
This is some pretty interesting data and highlights a few trends:
- Azure AD Connect has become the standard way to synchronize between Windows Server AD and Azure AD. Over 90 percent of synching tenants now use it.
- Azure AD Password Hash Sync has become a very popular option for our customers with tens of millions of monthly active users.
- As larger and larger enterprises have started using Azure AD, Ping Federate has become an increasingly popular option. Our partnership with Ping has really paid off for these large customers.
- Despite all the press coverage and market hype, other IDaaS vendors remain a very small part of the Azure AD/Office365 business.
- Our new Pass Through Authentication option, which only GAd a month ago is off to a good start with >500,000 MAU already! If current trends hold, sometime in the next six months to a year, it will be used by more unique users than all the other IDaaS vendors combined.
Summary
Just like last time, these numbers tell a pretty clear story. Weve designed Azure AD to be open and standards-based so our customers can use a wide variety of third-party options. However, the majority of customers find that our off the shelf identity solutions meet their needs. And this number continues to grow.
Additionally, the data also shows that the level of simplicity weve delivered with Azure AD Connect is having a big impact. The solution is being widely adopted and is far and away the fastest growing option for connecting Windows Server AD and Azure AD/Office 365.
Hopefully you found this blog post interesting and useful! As always, wed love to receive any feedback or suggestions you have.
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
Source: EM+S Blog Feed