Manage Google Play Protect with Microsoft Intune
Enabling the modern workplace means empowering our users to be productive from anywhere and on any device. Mobile devices are a great way to stay in touch with colleagues, catch up on email, or add the finishing touches to a project. With the power of having company data at your fingertips comes the responsibility of protecting the devices where that data is consumed.
Starting November 15th, IT Pros can leverage Microsoft Intune to ensure that Android devices accessing company data have enabled Google Play Protect services. Google Play Protect is a suite of security features provided by Google that enable enterprises to protect their devices, apps, and data. Lets now take a closer look at Google Play Protect and how you can control it with Intune.
Three pillars of Google Play Protect
- SafetyNet Verify Apps API Can my apps be trusted?
- Scans devices for known malicious app installations
- If it detects a potentially dangerous app, all users who have installed the app will be advised to remove it. You can learn more here.
- SafetyNet Attestation API Can my devices be trusted?
- Ensures Android devices pass Google’s compatibility and integrity checks
- Examines software and hardware on the device where the app is installed to create a profile of that device. The service then tries to match that profile against ones that passed Android compatibility testing to determine its integrity. The compatibility check API call returns a response that can be inspected for verification. You can learn more here.
- Google Play Services Are my communication channels secure?
- Ensures device Security Providers are up-to-date for secure network communications
- Enables SafetyNet Verify Apps API and SafetyNet Attestation API. You can learn more here.
Enable Google Play Protect compliance with Intune
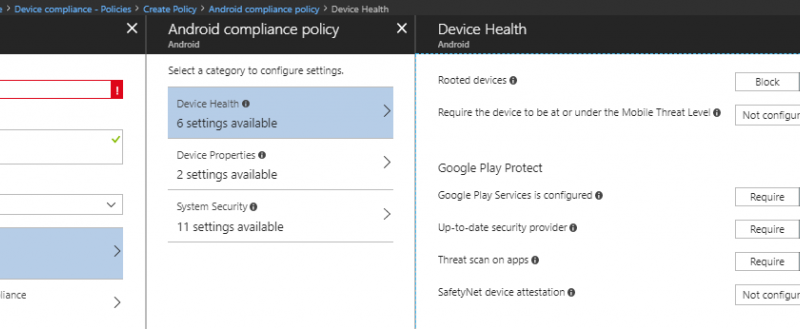
Intune integrates with Google Play Protect (GPP) services through the device compliance policies. To check for GPP compliance, you can create a new compliance policy for the Android platform. The four settings that belong to GPP can be found under the Device Health category.

A compliance policy that requires these settings can then be targeted to a group of Android users or devices. If a device does not have these settings enabled, it will fall out of compliance.
Google Play Protect compliance settings
- Google Play Services is configured
Check that the Google Play services app is installed and enabled. Google Play services allow security updates and is a base level dependency for many security features on certified Google devices. - Up-to-date security provider
An up-to-date security provider can protect a device from known vulnerabilities. - Threat scan on apps
This setting specifies whether to require that the Android “Verify Apps” feature is enabled.
NOTE: On the legacy Android platform, this feature is a compliance setting. Intune can only check to see whether this setting is enabled at the device level. On devices with work profiles (formerly Android for Work), this setting can be found as a configuration policy setting. This allows admins to enable the setting for a device. - SafetyNet device attestation
Set the level of SafetyNet device attestation integrity that must be met. There are two levels of device integrity that can be measured by Google Play Protect: basic integrity or basic integrity & certified devices.You can choose a less strict policy that requires that devices have a basic level of integrity, or you can choose a more stringent policy which ensures that devices have passed certification checks by Google. Understanding the differences between what basic integrity and Google compatibility measure is important because it can help you decide what the right level of policy is for your organization.
Google has published the following guidance about what these mean:
Check basic integrity tells you about the general integrity of the device. Rooted devices, emulators, virtual devices, and devices with signs of tampering fail basic integrity.
Check basic integrity & certified devices tells you about the compatibility of the device. Only unmodified devices that have been certified by Google can pass this check. Devices that will fail include the following:
- Devices that fail basic integrity
- Devices with an unlocked bootloader
- Devices with a custom system image/ROM
- Devices for which the manufactured didn’t apply for, or pass, Google certification
- Devices with a system image built directly from the Android Open Source Program source files
- Devices with a beta/developer preview system image
Enable Google Play Protect with Intune
If your organization supports devices that run Android work profiles (formerly Android for Work), Intune can take things one step further and enable the Threat scan on apps setting on your devices. To enable this setting, create a new device configuration profile for the Android for Work platform. Find Threat scan on apps under Device restrictions > System security.

A device configuration profile that requires Threat scan on apps will enable that setting on any device with a work profile that have the profile assigned to them.
Additional resources:
- Find technical documentation
- Ask questions and get answers in our Tech Community
- Follow us on Twitter for more frequent product updates
- Submit feedback and suggestions to our engineering team
Source: EM+S Blog Feed