Public preview of new Azure Policy features
In the week of the Microsoft Ignite Conference, we announced a private preview of a set of new features for Azure Policies in Azure Compute session, Azure Governance session, and Azure Resource Manager session. All of them are now in public preview.
Brand new Azure Policy UI with Continuous Monitoring
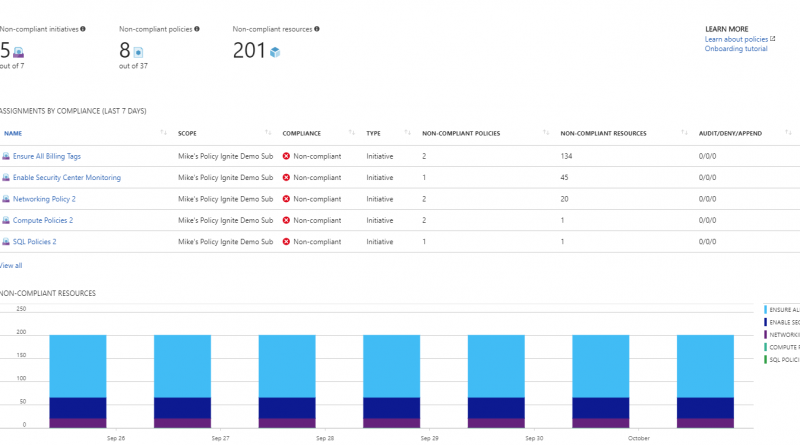
We have built a brand new user interface for Azure Policy that enables you to manage policies easily across all your subscriptions in a single place. In addition, you are able to continuously monitor compliance status of all your resources. This is very useful when you have a lot of resources that existed before you applied the policy. You can easily group your policies and look for the non-compliant resources. The policy engine constantly evaluates your resources and updates the compliance status. It also provides historical data in the dashboard. API support for historical data will be added in the future. In addition, the new UI supports a much richer set of policy management features, such as the creation of a custom policy. You can refer to this guide for new information.
Policy initiative and exclusion scope
A policy initiative can group a number of policy definitions. For example, the demo in Azure Resource Manager session groups the policies by resource types. Using initiatives greatly reduces the number of policy assignments you need to manage. These examples show you how to create and assign a policy initiative using PowerShell.
A policy exclusion allows you to assign policy at a high level and then exclude scopes within it. For example, in an environment with applications and central network, you want to have a policy for all application resource groups but not the network resource group. Previously, you had to assign different policies on all application resource groups. With exclusion scope, you can assign the policy at the subscription scope, so that even new application resource groups are automatically governed when they are created.
With the new policy management UI, you can directly create policy initiatives and apply exclusion scopes fro the portal.
Policy language enhancement
Additional resource type support
A lot of users may not know that the policy previously only evaluated for resource types that supported tags. It didn’t work for lots of nested resource types, such as subnets, diagnostic settings, SQL audit settings, etc. However, these resource types represent configurations that users need to enforce. With this new enhancement, the policy can be evaluated on all resource types when it is set to “all” mode. For any new policy you write, we recommend you use “all” mode to leverage the new support. For example, you can now enforce tags just on resource groups. Or, you can audit usage of a specific network security group for all your subnets.
Since these new resource types are typically nested, we also added two new policy effects so that policies can govern nested resources, and even related resources.
AuditIfNotExist
With AuditIfNotExist, a resource creation can trigger a deferred evaluation on other resources, including children resources. A typical use case is to audit all virtual machines that do not have anti-malware extension. An example is available on our GitHub.
DeployIfNotExist
With DeployIfNotExist, a policy provides a mechanism to automatically deploy a template if a specific configuration is not represented. For example, in the scenario above, a policy that leverages DeployIfNotExist effect can deploy the antimalware extension when a VM is created without it. Currently, DeployIfNotExist is only available through built-in policies. The deployment job runs on behalf of the user who created the resource. Custom policies will be supported in the future. Also, the deployment job will be able to run using its own identity in the future. The current available policies are:
- Deploy network watcher when virtual networks are created
- Deploy default Microsoft IaaSAntimalware extension for Windows Server
- Apply Diagnostic Settings for Network Security Groups
Azure Sample Policies GitHub repo
One challenge to adopting policies is constructing the JSON template. We created an Azure Policy Repository which contains quick-start samples from the community. Each sample policy contains instructions on how to use the policy. The policy also contains a “Deploy to Azure” button. Please join our effort to enrich the samples. Also, this is a great place to file issues and request additional features.
Try it out
Please try out the new features and let us know your thoughts and feedback!
Source: Azure Blog Feed