Security Center Playbooks and Azure Functions Integration with Firewalls
Every second counts when an attack has been detected. We have heard from you that you need to be able to quickly take action against detected threats. At Ignite 2017, we announced Azure Security Center Playbooks, which allow you to control how you want to respond to threats detected by Security Center. You can manually run a Security Center Playbooks when a Security Center alert is triggered, reducing time to response, and helping you stay in control of your security posture. Today, we are going to look at the specific example of how Azure Functions work with Security Center Playbooks to help you rapidly respond to detected threats against your Palo Alto VM-Series firewall.
In this scenario, Azure Security Center has detected and notified you of an RDP Brute Force attack. To help you block the source IP address of that attack in your Palo Alto VM-Series firewall, there are a couple steps you need to complete. You will first need to create an Azure Function which can be completed in the Functions Apps in the Azure portal, for HTTP Trigger using C# programming language. The Azure Function is what allows Security Center Playbooks to communicate with the Palo Alto VM-Series firewall and ultimately block malicious activity from traversing the firewall.
Next, place the sample code below in your Azure Function so that when you deploy a Security Center Playbook, your Playbook blocks the malicious IP from passing through the Palo Alto VM-Series firewall.
using System.Net;
using System.Security.Cryptography.X509Certificates;
using System.Net.Security;
public static async Task<HttpResponseMessage> Run(HttpRequestMessage req, TraceWriter log)
{
string key = "YOUR_PaloAlto_KEY";
string xmlElementForamt = @"
<source>
<member>{0}-{0}</member>
</source>
<destination>
<member>any</member>
</destination>
<application>
<member>any</member>
</application>
<service>
<member>any</member>
</service>
<action>deny</action>
<source-user>
<member>any</member>
</source-user>
<disabled>no</disabled>
<log-start>yes</log-start>
<log-end>yes</log-end>
<description>IP Blocked as response from Azure Security Center</description>
<from>
<member>any</member>
</from>
<to>
<member>any</member>
</to>";
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
dynamic data = await req.Content.ReadAsAsync<object>();
string ip = data?.ip;
string ruleName = string.Format("IP {0} blocked from ASC", ip);
string xmlElement = string.Format(xmlElementForamt, ip);
string url = string.Format(
"https://YOUR_PALO_ALTO_URL/api/?type=config&action=set&key={0}&xpath=/config/devices/entry/vsys/entry/rulebase/security/rules/entry[@name='{1}']&element={2}",key, ruleName, xmlElement);
var request = (HttpWebRequest)WebRequest.Create(Uri.EscapeUriString(url));
request.ServerCertificateValidationCallback += (object sender, X509Certificate certificate, X509Chain chain, SslPolicyErrors sslPolicyErrors) => true;
var response = (HttpWebResponse)(await request.GetResponseAsync());
response.Close();
return req.CreateResponse(HttpStatusCode.OK);
}
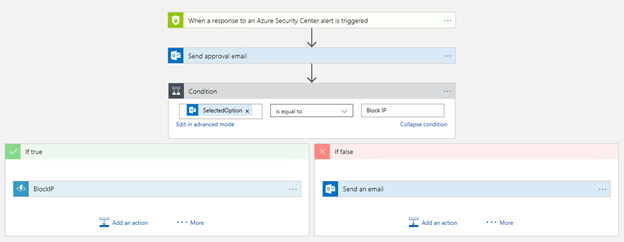
Now that your sample code is in your Azure Function, you need to go to the Security Center to create a new Playbook with the workflow shown below. The Playbook defines how you orchestrate your response to issues with your Palo Alto firewall.
As shown above, when an alert is generated, an approval email is sent to the security administrator asking if she or he wants to block or ignore the source IP of the attack. If the answer for to that email is block, the Azure Function that was created will receive the source IP and create a blocking rule in the Palo Alto VM-Series firewall. If the answer for that approval email is ignore, another email will be send to the security administrator with an alert description.
Now when a security alert is triggered, because Azure Functions and a Playbook are set up, you can quickly respond to the detected threats by creating a blocking rule in your Palo Alto VM-Series firewall, and stay in control of your network security.
For more information about playbooks and functions, visit our documentation.
To get started with Azure Security Center Playbooks, try the Standard tier of Security.
Source: Azure Blog Feed