Improvements to the protection stack in Azure Information Protection
Were constantly striving to make the process of protecting information easier and simpler for both users and admins. To help with the initial step in protecting your information, we’re happy to announce that starting February 2018 all Azure Information Protection eligible tenants will have Azure Information Protection on by default. Any organization which has Office E3 and above or EMS E3 and above service plans can now get a head start in protecting information through Azure Information Protection.
The new version of Office 365 Message Encryption which was announced at Microsoft Ignite 2017, leveraged the encryption and protection capabilities of Azure Information Protection. We have continued to make significant improvements in the product since its initial launch and are excited to announce new capabilities in both Office 365 Message Encryption and Azure Information Protection.
Protection on by default
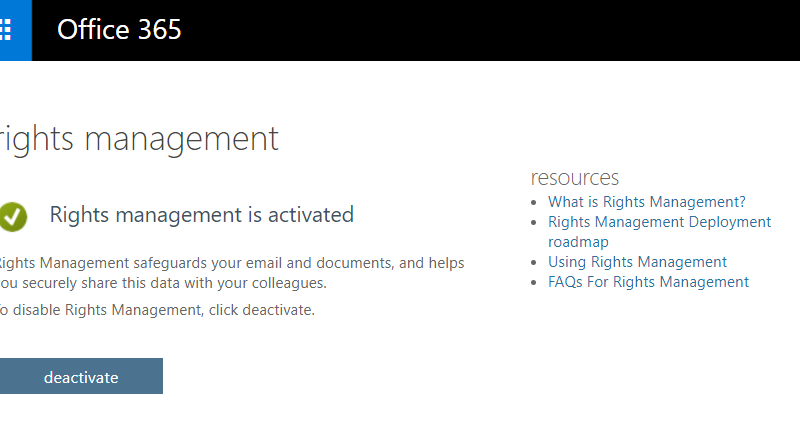
Starting February 2018, Microsoft will enable the protection capability in Azure Information Protection automatically for our new Office 365 E3 or above subscription. Tenant administrators can check the protection status in the Office 365 administrator portal.

EMS E3/E5 subscription and Azure Information Protection P1, P2 plans offer standardized and approachable labels and classification taxonomy. The default global policy will now configures Azure Information Protection based encryption and rights management for the following sublabels:
- Confidential All Employees
- Confidential Recipients Only
- Highly Confidential All Employees
- Highly Confidential Recipients Only
Please refer to our documentation for more details.

Office Message Encryption on by default
Along with enabling the protection service, Microsoft has now enabled the Office 365 Message Encryption capabilities by default for any new Office E3 or above subscription.

Richer collaboration specifically for email scenarios
Azure Information Protections powerful classification andlabelling capabilities enabled organizations to easily collaborate within and across organizational boundaries. Administrators could create labels which were backed by protection policies which promoted group-collaboration (e.g finance@contoso.com) and cross company-collaboration (e.g fabrikam.com). However, until now, the groups and users specified in the label definitions (e.g fabrikam.com, finance@contoso.com) needed to be part of the AAD identity fabric.
Since Microsoft Ignite 2017, Office 365 Message Encryption has enabled organizations to send Azure Information Protection encrypted and rights managed emails to anyone with any email address. However, administrators expressed their frustration on their inability to create effective Azure Information Protection labels which was backed with protection that could include non-AAD users and groups. With this month’s update of the Azure Information Protection service, administrators can now include non-AAD domains in the template definition which would specifically assist in cross-company or non-AAD collaboration scenarios of Office 365 Message Encryption. In the snip below, Contosos administrator has defined a custom protection permission for recipients who have a gmail.com address, hotmail.com address and onpremcompany.com address.

New policy Encrypt-Only
Do Not Forward has been the only out-of-box and default policy which was available to our customers. While Do Not Forward is very useful in securing the content (recipients cannot forward, print, edit, copy content), customers have indicated that it is far too restrictive and does not help in todays collaborative environment.
We are releasing a new out-of-the-box policy called Encrypt-only. With this policy, users can send encrypted email to any recipient, whether they are inside or outside the organization, and the protection follows the lifecycle of the email. However, unlike Do Not Forward, recipients can copy, print and forward the email. Encryption will follow the forwarded mail and no one other than the original sender can remove the protection of the email. This new policy provides more flexibility in the type of protection that can be applied to your sensitive emails. You can learn more about the Encrypt-Only policy here.
A few questions you might have:
How does this announcement for enabling Azure Information Protection by default affect existing Office 365 tenants?
There is no impact to existing Office 365 tenant. They would still need to enable Azure Information Protection manually through Office 365 or through PowerShell cmdlets.
However, for tenants who have enabled Azure Information Protection, Office 365 Message Encryption will be enabled by default.
How does it affect tenants who wish to migrate from AD RMS to Azure Information Protection?
Going forward, if you are creating a cloud subscription for migrating from AD RMS to Azure RMS, please manually disable the Rights Management service before starting the migration.
Will SharePoint Online IRM feature also be configured automatically?
No, that still needs to be done manually.
We feel these updates will reduce the work admins need to do to secure emails within organizations. Let us know if you have any feedback and well try our best to improve your experiences. Engage with us on Yammer or Twitter and let us know whats important to you by voting on UserVoice!
Source: EM+S Blog Feed