How Azure Security Center helps detect attacks against your Linux machines
Azure Security Center (ASC) is now extending its Linux threat detection preview program, both on cloud and on-premise. New capabilities include detection of suspicious processes, suspect login attempts, and anomalous kernel module loads. Security Center is using auditd for collecting machines’ events, which is one of the most common frameworks for auditing on Linux. Auditd has the advantage of having been around for a long time and living in the mainline kernel. Any Linux machine that runs auditd by default and is covered by Security Center will benefit from this public preview. For a little more detail on how the collection works, check out our private preview announcement from October.
In addition to building up Linux-specific detections, we have also reviewed applicability of our current detections originally developed for Windows. Attackers also like to be OS-agnostic, especially for large-scale attacks, and will reuse tools and techniques where they can. In such circumstances the same detection is also applicable across operating systems. Happily, several of our analytics worked with minimal tuning. Today, I’ll walk you through an analytic example in the form of malicious crypto coin mining and then give some tips on using Azure Log Analytics with Linux machines.
The expanding threat of malicious crypto coin miners
The Windows Defender Research team published a blog post last month talking about the increasing threat of crypto currency miners. These resource thieves have become more of an issue as cryptocurrencies have increased in number and value. The Windows Defender team notes that it appears some cybercriminals are pivoting from ransomware attacks to installing and running their own mining tools on victim machines. Between September 2017 and January 2018, they saw an average of 644,000 unique computers encountering coin mining malware. The post goes on to talk about some of the different coin mining malware we have seen, how they operate, and how enterprises can defend themselves using both System Center Configuration Manager and Windows Defender Advanced Threat Protection.
Also last month, the Windows Defender team talked about how, on March 6, Windows Defender Antivirus identified, within milliseconds, and blocked nearly 500,000 instances of a Dofoil malware campaign. This malware also contained a coin mining payload. Later, it was discovered and reported that the initial infection vector was a poisoned peer-to-peer application. The peer-to-peer application was classified as a potentially unwanted application (PUA). Windows Defender AV customers who had enabled the PUA protection feature, benefited as that vector was already blocked.
Azure Security Center threat detections for Linux
So how does this relate to Azure and the public preview of our new Azure Security Center threat detections for Linux? One year ago, Jessen Kurien posted about how we are detecting crypto currency mining attacks in ASC for Windows machines. In the crypto currency malware industry, a lot of cybercriminals are using portable tools that will install and run on different operating systems based on where they get dropped. They are also utilizing common techniques across systems which means there is an opportunity to write common detections.
In February, FireEye published a blog post that very neatly shows how these mining tools and techniques are spanning both the Windows and Linux worlds. In their overview, you can see both Windows-based PowerShell commands and Bash shell script commands for downloading additional malware, scheduling tasks, and deleting competing malware. Analysis of our own data shows the same thing. These common techniques give us the opportunity to create analytics that either work for both Windows and Linux machines.
When creating analytics, we also try to identify the malicious behavior at multiple points in its lifecycle which increases the likelihood of a detection. Our crypto currency mining analytic is a good example of this. We started with simple executable or command matching then gradually increased the level of sophistication of the analytic and created detections that look for coin mining behavior. One of our more recent analytics tries to detect when a system is being optimized for coin mining.
Linux alerts in Azure Security Center
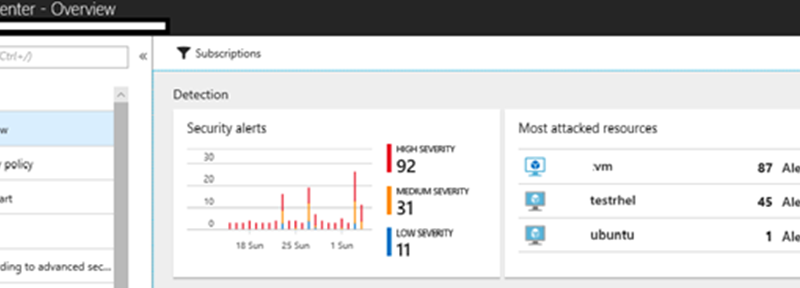
So how do we see these crypto coin mining alerts in Linux? Azure Security Center customers that have Linux machines running auditd will be able to see these alerts alongside other Azure Security Center alerts. Just go into the Azure Security Center Overview page.
Then, either click into your subscription alerts through New Alerts & Incidents, Detections, or dive right into a specific resource.
The alert for crypto coin malware will show up as the Suspicious Process Executed alert that you can see below.
When you click through into the alert, you will see the process and command line that triggered the alert, as well as suggested remediation steps.
As you can see, this event triggered as a Suspicious Process execution. You can see the command that was run in the Description and the specific command line down below. Also, because we recognize this as crypto coin mining behavior, we have linked to a report on Bitcoin Miners.
Tips for using Azure Log Analytics with Linux
Earlier this year, Ajeet Prakash posted an article about how to utilize Azure Log Analytics while investigating Azure Security Center alerts. He walked through how to drill into a security alert as part of an investigation, and how to get to the recorded Windows logs through Azure Log Analytics. You have the same ability to do this for your Linux machines. There are some differences you will want to be aware of to get the most out of Azure Log Analytics when looking at Linux machines and I’ve highlighted a couple of the key ones below.
When running Security Baseline searches (1.) you can call out specifically the BaselineType field to just look at the results for your “WindowsOS” or “Linux” machines. When you want to look at Linux logs specifically, you will need to pull the information from the LinuxAuditLog under the Security drop down. If you are writing out your query, use LinuxAuditLog (2.) as your source. If you look in the table of the image below, you can see there are a number of record types available to look at under LinuxAuditLog.
For more information about writing queries, check out the Azure Log Analytics Getting Started page.
More resources
That is a quick intro to the new Linux analytics for Azure Security Center. We’ve walked through a crypto currency example and shown how you can still utilize tools like Azure Log Analytics for investigations. Many of the things you are used to from the Windows side carry over and should seem familiar. For more information about how Azure Security Center works see the following:
- Azure Security Center detection capabilities — Learn about Azure Security Center’s advanced detection capabilities.
- Managing and responding to security alerts in Azure Security Center — Learn how to manage and respond to security alerts.
- Managing security recommendations in Azure Security Center — Learn how recommendations help you protect your Azure resources.
- Security health monitoring in Azure Security Center — Learn how to monitor the health of your Azure resources.
- Monitoring partner solutions with Azure Security Center — Learn how to monitor the health status of your partner solutions.
- Azure Security Center FAQ — Find frequently asked questions about using the service.
- Azure Security blog — Get the latest Azure security news and information.
Source: Azure Blog Feed