Introducing the redesigned Security Center Overview dashboard
Azure Security Center’s dashboard has been redesigned to provide cross-subscription, organizational level reports of the most important metrics that influence the organizational security posture, as well providing actionable insights to help organizations improve their overall security posture.
The redesigned dashboard also introduces two new concepts in Security Center:
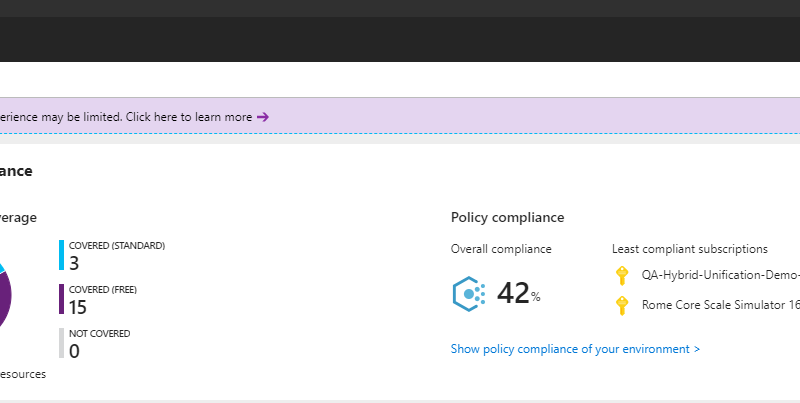
Subscription Coverage: This metric presents the Security Center status of all subscriptions the user has (at least) read access to and helps identify subscriptions lack adequate security controls. NOTE: In order to gain visibility to all subscriptions under your AAD tenant, it is required to set either a Reader, Security Reader or Security Administrator role on the root Management Group. To learn more about the Azure Management Groups integration with Security Center, visit Integrate Security Center security policies with Azure Policy.
Policy Compliance: This metric conveys the organization’s adherence to the security policies assigned to its resources. 
Actionable insights reside on the right-hand side of each of their respective areas and include the following:
Policy and compliance: Policy compliance over time, connecting Security Center to a SIEM solution and a guide to using security policies in Security Center
Resource security hygiene: Most prevalent recommendations and highest impact recommendations
Threat protection: Most prevalent alerts, subscriptions that have no security contact defined

These insights highlight areas that can assist an organization identify the actions the organization may take in order the improve its overall security posture, for example:
- A common security hygiene issue that affects a large number of resources – the organization can launch a campaign to deploy an endpoint protection solution all across its VMs, or enabling encryption on its data/storage assets
- A resource that is frequently getting attacked (therefore having many alerts) – strengthen the protection around it to reduce the attack surface
- A change in the trend of the organization’s overall compliance in specific points in time – identify the events that cause the overall compliance to change and address them – for example, an event where a new application was launched, which included multiple resources that do not comply to the organizational security policy, and ensuring future launches will be compliant from the get go
For additional information about the new design, metrics and usage of Azure Policies in Security Center, please refer to the following articles:
Get started with Azure Security Center today.
Source: Azure Updates