Scale Azure Firewall SNAT ports with NAT Gateway for large workloads
This post was co-authored by Suren Jamiyanaa, Product Manager II, Azure Networking.
As large organizations across all industries expand their cloud business and operations, one core criteria for their cloud infrastructure is to make connections over the internet at scale. However, a common outbound connectivity issue encountered when handling large-scale outbound traffic is source network address translation (SNAT) port exhaustion. Each time a new connection to the same destination endpoint is made over the internet, a new SNAT port is used. SNAT port exhaustion occurs when all available SNAT ports run out. Environments that often require making many connections to the same destination, such as accessing a database hosted in a service provider’s data center, are susceptible to SNAT port exhaustion. When it comes to connecting outbound to the internet, customers need to not only consider potential risks such as SNAT port exhaustion but also how to provide security for their outbound traffic.
Azure Firewall is an intelligent security service that protects cloud infrastructures against new and emerging attacks by filtering network traffic. All outbound internet traffic using Azure Firewall is inspected, secured, and undergoes SNAT to conceal the original client IP address. To bolster outbound connectivity, Azure Firewall can be scaled out by associating multiple public IPs to Azure Firewall. Some large-scale environments may require manually associating up to hundreds of public IPs to Firewall in order to meet the demand of large-scale workloads, which can be a challenge to manage long-term. Partner destinations also commonly have a limit on the number of IPs that can be whitelisted at their destination sites, which can create challenges when Firewall outbound connectivity needs to be scaled out with many public IPs. Without scaling this outbound connectivity, customers are more susceptible to outbound connectivity failures due to SNAT port exhaustion.
This is where network address translation (NAT) gateway comes in. NAT gateway can be easily deployed to an Azure Firewall subnet to automatically scale connections and filter traffic through the firewall before connecting to the internet. NAT gateway not only provides a larger SNAT port inventory with fewer public IPs but NAT gateway’s unique method of SNAT port allocation is specifically designed to handle dynamic and large-scale workloads. NAT gateway’s dynamic allocation and randomized selection of SNAT ports significantly reduce the risk of SNAT port exhaustion while also keeping overhead management of public IPs at a minimum.
In this blog, we’ll explore the benefits of using NAT Gateway with Azure Firewall as well as how to integrate both into your architecture to ensure you have the best setup for meeting your security and scalability needs for outbound connectivity.
Benefits of using NAT Gateway with Azure Firewall
One of the greatest benefits of integrating NAT gateway into your Firewall architecture is the scalability that it provides for outbound connectivity. SNAT ports are a key component to making new connections over the internet and distinguishing different connections from one another coming from the same source endpoint. NAT gateway provides 64,512 SNAT ports per public IP and can scale out to use 16 public IP addresses. This means, when fully scaled out with 16 public IP addresses, NAT gateway provides over 1 million SNAT ports. Azure Firewall, on the other hand, supports 2,496 SNAT ports per public IP per virtual machine instance within a virtual machine scale set (minimum of 2 instances). This means that to achieve the same volume of SNAT port inventory as NAT gateway when fully scaled out, Firewall may require up to 200 public IPs. Not only does NAT gateway offer more SNAT ports with fewer public IPs, but these SNAT ports are allocated on demand to any virtual machine in a subnet. On-demand SNAT port allocation is key to how NAT gateway significantly reduces the risk of common outbound connectivity issues like SNAT port exhaustion.
NAT gateway also provides 50 Gbps of data throughput for outbound traffic that can be used in line with a standard SKU Azure Firewall, which provides 30 Gbps of data throughput. Premium SKU Azure Firewall provides 100 Gbps of data throughput.
With NAT gateway you also ensure that your outbound traffic is entirely secure since no inbound traffic can get through NAT gateway. All inbound traffic is subject to security rules enabled on the Azure Firewall before it can reach any private resources within your cloud infrastructure.
To learn more about the other benefits that NAT gateway offers in Azure Firewall architectures, see NAT gateway integration with Azure Firewall.
How to get the most out of using NAT Gateway with Azure Firewall
Let’s take a look at how to set up NAT gateway with Azure Firewall and how connectivity to and from the internet works upon integrating both into your cloud architecture.
Production-ready outbound connectivity with NAT Gateway and Azure Firewall
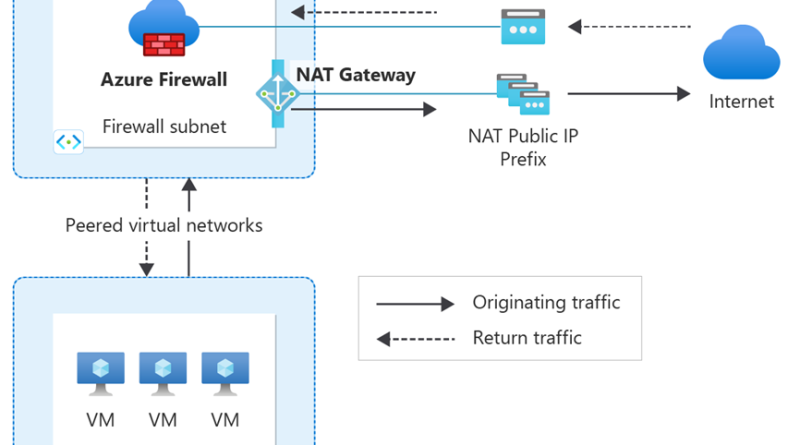
For production workloads, Azure recommends separating Azure Firewall and production workloads into a hub and spoke topology. Introducing NAT gateway into this setup is simple and can be done in just a couple short steps. First, deploy Azure Firewall to an Azure Firewall Subnet within the hub virtual network (VNet). Attach NAT gateway to the Azure Firewall Subnet and add up to 16 public IP addresses and you’re done. Once configured, NAT gateway becomes the default route for all outbound traffic from the Azure Firewall Subnet. This means that internet-directed traffic (traffic with the prefix 0.0.0.0/0) routed from the spoke Vnets to the Hub Vnet’s Azure Firewall Subnet will automatically use the NAT gateway to connect outbound. Because NAT gateway is fully managed by Azure, NAT gateway allocates SNAT ports and scales to meet your outbound connectivity needs automatically. No additional configurations are required.
Figure: Separate the Azure Firewall from the production workloads in a hub and spoke topology and attach NAT gateway to the Azure Firewall Subnet in the hub virtual network. Once configured, all outbound traffic from your spoke virtual networks is directed through NAT gateway and all return traffic is directed back to the Azure Firewall Public IP to maintain flow symmetry.
How to set up NAT Gateway with Azure Firewall
To ensure that you have set up your workloads to route to the Azure Firewall Subnet and use NAT gateway for connecting outbound, follow these steps:
- Deploy your Firewall to an Azure Firewall Subnet within its own virtual network. This will be the Hub Vnet.
- Add NAT gateway to the Azure Firewall Subnet and attach at least one public IP address.
- Deploy your workloads to subnets in separate virtual networks. These virtual networks will be the spokes. Create as many spoke Vnets for your workload as needed.
- Set up Vnet peering between the hub and spoke Vnets.
- Insert a route to the spoke subnets to route 0.0.0.0/0 internet traffic to the Azure Firewall.
- Add a network rule to the Firewall policy to allow traffic from the spoke Vnets to the internet.
Refer to this tutorial for step-by step guidance on how to deploy NAT gateway and Azure Firewall in a hub and spoke topology.
Once NAT gateway is deployed to the Azure Firewall Subnet, all outbound traffic is directed through the NAT gateway. Normally, NAT gateway also receives any return traffic. However, in the presence of Azure Firewall, NAT gateway is used for outbound traffic only. All inbound and return traffic is directed through the Azure Firewall in order to ensure traffic flow symmetry.
FAQ
- Can NAT gateway be used in a secure hub virtual network architecture with Azure Firewall?
- No, NAT gateway is not supported in a secure hub (vWAN) architecture. A hub virtual network architecture as described above must be used instead.
- How does NAT gateway work with a zone-redundant Azure Firewall?
- NAT gateway is a zonal resource that can provide outbound connectivity from a single zone for a virtual network regardless of whether it used with a zonal or zone-redundant Azure Firewall. To learn more about how to optimize your availability zone deployments with NAT gateway, refer to our last blog.
Benefits of NAT Gateway with Azure Firewall
When it comes to providing outbound connectivity to the internet from cloud architectures using Azure Firewall, look no further than NAT gateway. The benefits of using NAT gateway with Azure Firewall include:
- Simple configuration. Attach NAT gateway to the Azure Firewall Subnet in a matter of minutes and start connecting outbound right away. No additional configurations required.
- Fully managed by Azure. NAT gateway is fully managed by Azure and automatically scales to meet the demand of your workload.
- Requires fewer static public IPs. NAT gateway can be associated with up to 16 static public IP addresses which allows for easy whitelisting at destination endpoints and simpler management of downstream IP filtering rules.
- Provides a greater volume of SNAT ports for connecting outbound. NAT gateway can scale to over 1 million SNAT ports when configured to 16 public IP addresses.
- Dynamic SNAT port allocation ensures that the full inventory of SNAT ports is available to every virtual machine in your workload. This in turn helps to significantly reduce the risk of SNAT port exhaustion that is common with other SNAT methods.
- Secure outbound connectivity. Ensures that no inbound traffic from the internet can reach private resources within your Azure network. All inbound and response traffic is subject to security rules on the Azure Firewall.
- Higher data throughput. A standard SKU NAT gateway provides 50 Gbps of data throughput. A standard SKU Azure Firewall provides 30 Gbps of data throughput.
Learn more
For more information on NAT Gateway, Azure Firewall, and how to integrate both into your architectural setup, see:
- What is Azure Virtual Network NAT?
- Azure Firewall documentation.
- Scale SNAT ports with Azure Virtual Network NAT.
- Integrate NAT gateway with Azure Firewall in a hub and spoke network.
Source: Azure Blog Feed