Lots of News about Azure AD B2C feature updates!
Howdy folks,
Today Im excited to let you know about a passel of new features weve just turned on our Azure AD B2C service! These features give you a ton of new options for customizing your Azure AD B2C end user experience.
We have some highly demanded features going into public preview:
- Custom password complexity
- B2C specific audit events in the Azure portal
- GitHub as an identity provider
And some features that you may already be familiar with, are now Generally Available (GA):
Finally, weve made some improvements in two features currently in public preview:
To learn more about all these features scroll down below or visit our documentation.
Custom password complexity
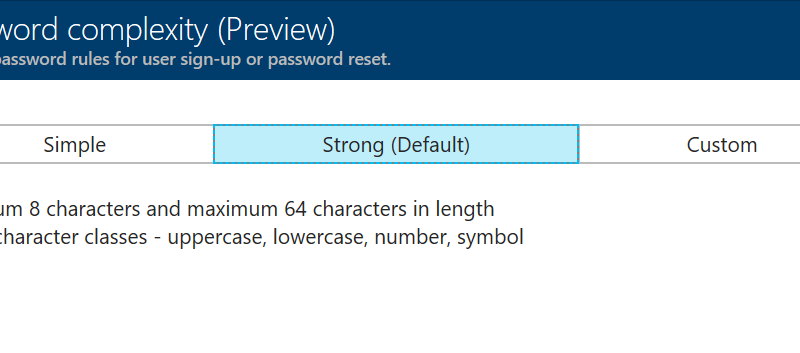
On each policy you now have access to a new blade that looks like this:

By default, all policies have strong password requirements which are shown above. If you set this to simple, it only enforces a password of 8-64 characters with no requirements for character types and cases. These new requirements are enforced when a user signs up or changes their password.
Or you can customize your own level of password security:

The error messages for passwords have also been improved so that it will direct your users to the requirements they still need to fill:

This feature is now in Public Preview.
B2C audit events in the Azure portal
We’re in the process of adding more audit logs into the Azure portal or via API! For the first phase we are now logging events for:
- ID token issuance
- Access token issuance
- Authorization code issuance
- Local and social account login events (through sign up or sign in policy)
We plan to be adding more and if you have feedback on how we can improve our existing events or what events you would like to see, please send your feedback to feedback.azure.com. As we introduce these additions we will also be deprecating the reporting API, you can find more information here.
This feature is now in Public Preview.
GitHub as an Identity provider
You can now configure GitHub as an identity provider in built-in policies!

Migrate users with social identities
You can now write to the altsecid user property in AAD graph. This property allows users to have multiple social accounts tied to their local user account. This means that if you currently have users with social identities in your existing solutions, you can migrate them to Azure AD B2C while keeping their social account linked.
This feature is now Generally Available.
Twitter as an identity provider
A ton of consumers are now using Twitter as an identity provider in Azure AD B2C, weve completed our quality assurance work and this feature is now Generally Available.
Language customization
We have made the last batch of major updates to language customization which we are previewing now. Once we’ve had enough time to act on your feedback before we will announce general availability. We have updated the UX to be easier for you to configure each individual language:

UX changes:
- You can now upload/download language resources for all relevant pages for a single language in a single context pane
- You can download your existing overrides for all languages
- The enable page will now be incorporated with the blade and no longer have a warning
Custom locales
We have also added a feature which allows you add your own support for languages and regional variants which we don’t provide translations for! Just click the ‘Add custom language’ button at the top and assign it a locale code for a language we don’t support. After that, you provide language resources just like any supported language, except you have to provide all the translations.
You can learn more about this feature here.
Access tokens
Were simplifying the configuration experience for access tokens as we move the feature to GA this month. To learn more about access tokens, visit theaccess tokens documentation page.
You can try all these features right now by going to the Azure portal to create your own Azure AD B2C tenant! As always, wed love to receive any feedback or suggestions you have!
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
Source: EM+S Blog Feed