Conditional access in Azure AD: macOS support plus two more features now generally available!
Howdy folks!
Device-based conditional access is one of the hottest features in Azure AD and is growing at a rapid pace. Today, Im excited to announce the general availability of a set of capabilities for device- and app-based conditional access that many of you have been eagerly waiting for.
- Support for macOS device-based conditional access
- Application-based conditional access for limiting access to managed apps with in-app controls for iOS and Android
- The Devices blade in Azure AD in Azure portal
macOS as platform for device-based conditional access
Now you can comprehensively secure access to Office 365 and other Azure AD-connected apps with new support for macOS conditional access. With macOS conditional access you have the ability to:
- Enroll and manage macOS devices using Intune
- Ensure macOS devices adhere to your organizations compliance policies defined in Intune
- Restrict access to applications in Azure AD to only compliant macOS devices
Whats new in GA
Chrome as a supported browser: In public preview, we started with supporting only the Safari browser. With general availability, we’re extending support for device-based conditional access to Chrome on macOS.
Microsoft Teams: Microsoft Teams is now a supported application, in addition to the applications supported during the public preview of conditional access for macOS.
An improved Intune Company Portal: The Intune Company Portal on macOS has an updated experience, which has been optimized to cleanly display all the information and compliance notifications your users need for all the devices they have enrolled. And, once the Intune Company Portal has been deployed to a device, Microsoft AutoUpdate for macOS will provide updates to it.
You can download the new Intune Company Portal for macOS by logging into the Intune Company Portal website from a macOS device.
Note: Updating from the preview version of the Company Portal will not require users to re-enroll into Intune.
The following OS versions, applications, and browsers are supported on macOS for conditional access:
Operating Systems
- macOS 10.11+
Applications
- Microsoft Office 2016 for macOS v15.34 and later
- Microsoft Teams
Browsers
- Safari
- Chrome
Azure AD application-based conditional access for iOS and Android in the Azure portal
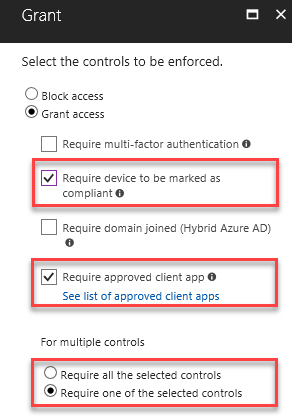
With today’s update, you can now restrict access to Office 365 and other Azure AD-connected cloud apps from approved client apps that support Intune App Protection policies using Azure AD app-based conditional access. Intune App Protection policies are used to configure and protect company data on these client applications.
You also get the flexibility to protect data for both personal and company devices by combining app-based conditional access policies with a device-based policy.

Whats in GA
The following conditions and controls are now available for use with app-based conditional access:
Supported platform condition
- iOS
- Android
Client apps condition
- Mobile apps as supported client apps
Access control
- Require approved client app
Learn how to set up a combined policy on Azure AD for Microsoft Exchange Online and Microsoft SharePoint Online.
Devices blade in Azure AD in Azure portal
With this last feature, you’re now able to find all your devices and device-related activities in one place: a new blade for management of device identities in the Azure portal. In this new blade, you can:
- View all your devices that are available for conditional access in Azure AD
- View properties, including your Hybrid Azure AD-joined devices
- Find BitLocker keys for your Azure AD-joined devices, manage your device with Intune and more
- Manage Azure AD device-related settings
Find the new ‘Devices’ option in the Azure portal under Azure Active Directory.

Try these features out today and let us know what you think! We look forward to hearing from you.
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
Quick Links
- macOS Company Portal
- macOS Compliance Policy authoring
- Authoring conditional access policy
- App-based conditional access technical documentation
- App protection policies in Intune
- Device management Introduction
Source: EM+S Blog Feed