Cloud App Security Threat Protection just got better
As we have conversations with Security Operations (SecOps) teams, were seeing a notable shift in the approach to threat detection and protection: moving from a technology-driven, product-focused approach to a use-case driven approach. These teams define their pain points carefully and invest in solutions that address these key needs.
As we all know, the more visibility you gain into your users activities, the better control you have. To this extent, we constantly innovate to provide better visibility, control, and protection to your cloud apps. Today, we are happy to share exciting new enhancements in our threat protection capabilities that take our investigation and remediation for cloud apps to the next level.
What are the new enhancements in the threat detection?
Over the last year we re-designed the threat protection and anomaly detection engine in Microsoft Cloud App Security and Office 365 Cloud App Security, leveraging knowledge from Microsofts Intelligent Security Graph. Cloud App Security now helps detect the most sophisticated threats in your cloud apps faster. In addition, it allows us to expose more data from our detection engine, to help you speed up the investigation process and contain ongoing threats.
So, what are these changes specifically?
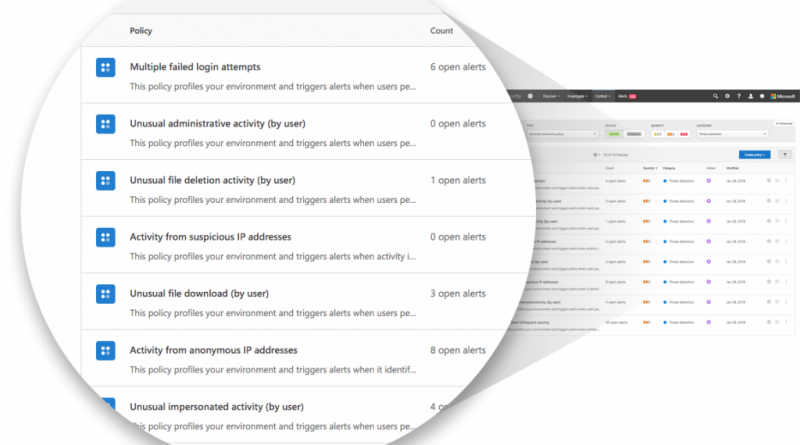
For an enhanced admin user experience, weve introduced several new policies. Each of these policies represents a different detection and a use-case scenario. For example impossible travel, multiple failed login attempts, activity from suspicious IP. This aligns Cloud App Security with the use-case driven approach SecOps teams demand, as each detection represents a key security use case.
All the new policies include learning mechanisms to reduce false positive alerts, so you can focus on what is most important. These policies will replace our General Anomaly detection policies, but you will still be able to see all the historic alerts that you currently have.

Figure 1. Cloud App Security threat detection new alerts
You also want to have all the information possible, so you can triage the different alerts quickly and decide which ones need to be taken care of first. To do this, youll need the context for the alert so you will be able to see the bigger picture and understand whether something malicious is indeed happening.
To help with this, we have made improvements to the alert investigation capabilities in the activity log with the newly added User Insights. This includes information like number of alerts, activities, and where they have connected from, which is important in an investigation.

Figure 2.Cloud App Security Activity log, User Insights
Now you can easily understand what the suspicious activities that the user was performing and gain deeper confidence as to whether the account was compromised. For example, an alert on multiple failed logins may indeed be suspicious and can indicate potential brute force attack, but it can also be an application misconfiguration, causing the alert to be a benign true positive. However, if you see a multiple failed logins alert with additional suspicious activities, then there is a higher probability that the account is compromised. In the example below, you can see that the Multiple failed login attempts alert was followed by Activity from a TOR IP address and Impossible travel activity, both strong indicators of compromise (IOCs) by themselves. If this wasnt suspicious enough, then we can see that the same user performed a Mass download activity, which is often an indicator of the attacker performing exfiltration of data.

Figure 3.Example user alerts
Learn more
If you have Microsoft Cloud App Security or Office 365 Cloud App Security deployed, you will see these features already enabled in your tenant. If not, you can try Microsoft Cloud App Security and Office 365 Cloud App Security for 90-days with no additional cost and see how this service helps you with providing visibility, data control and threat protection to your cloud apps.
Our goal in the Cloud App Security engineering team is to continuously innovate to provide a top-notch user experience, visibility, data control and threat protection to your cloud apps.
If you would like to learn more, visit the technical documentation for Microsoft Cloud App Security and Office 365 Cloud App Security.
We love hearing your feedback. Get started today, give these new features a try and let us know what you think at Microsoft Cloud App Security Tech Community.
Source: EM+S Blog Feed